Azure Security Center: 7 Powerful Features You Must Know
Managing cloud security can feel overwhelming, but Azure Security Center makes it simpler, smarter, and more powerful than ever. It’s not just a tool—it’s your proactive guardian in the cloud.
Azure Security Center Overview
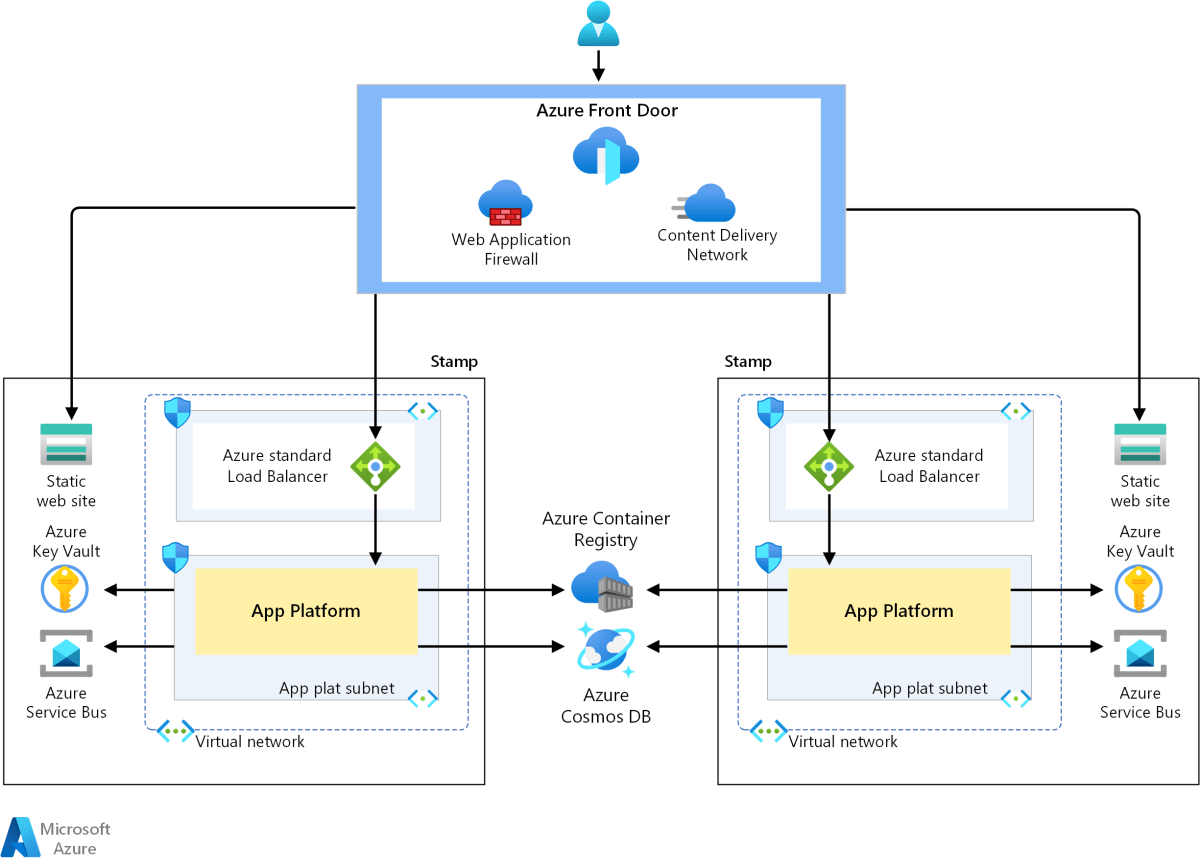
Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers and provides advanced threat protection across hybrid cloud workloads. Whether your resources are on Azure, on-premises, or in other clouds, Security Center offers visibility and control over security risks.
What Is Azure Security Center?
Azure Security Center is a cloud-native security information and event management (SIEM) and security orchestration and automated response (SOAR) platform. It integrates deeply with Azure services and extends protection to non-Azure environments through agents and connectors. It continuously monitors your environment, assesses security posture, detects threats, and recommends actions to reduce vulnerabilities.
Originally launched as part of Microsoft’s Azure cloud platform, Security Center evolved into Microsoft Defender for Cloud—a unified platform that combines cloud workload protection with cloud security posture management. However, many still refer to it as Azure Security Center due to its foundational role and widespread adoption.
Key Components of Azure Security Center
The platform is built around three core components: security posture management, threat protection, and security management. These components work together to provide a comprehensive view of your organization’s security health.
- Security Posture Management: Assesses your resources against security best practices and compliance standards.
- Threat Protection: Uses behavioral analytics and machine learning to detect suspicious activities and potential breaches.
- Security Management: Centralizes security policies, alerts, and recommendations across subscriptions and workloads.
These components are accessible through the Azure portal, where administrators can view dashboards, configure policies, and respond to incidents in real time. For more information, visit the official Microsoft Defender for Cloud documentation.
“Azure Security Center gives you a clear view of your security state across all your Azure resources, on-premises, and other clouds.” — Microsoft Azure Documentation
Core Benefits of Using Azure Security Center
Organizations adopt Azure Security Center because it simplifies complex security operations while enhancing protection. Its value lies in automation, integration, and intelligence.
Unified Security Management Across Environments
One of the biggest challenges in modern IT is managing security across hybrid and multi-cloud environments. Azure Security Center bridges this gap by offering a single pane of glass for monitoring and managing security across Azure VMs, on-premises servers, AWS EC2 instances, and GCP workloads.
By connecting non-Azure machines via the Log Analytics agent or Azure Arc, Security Center extends its reach beyond Azure. This unified approach eliminates silos and ensures consistent policy enforcement regardless of where workloads reside.
Automated Security Recommendations
Azure Security Center continuously analyzes your environment and generates actionable recommendations. These include suggestions like enabling disk encryption, configuring network security groups, or installing endpoint protection.
Each recommendation includes severity levels (High, Medium, Low), affected resource counts, and step-by-step remediation guidance. You can even automate fixes using Azure Policy and Logic Apps, reducing manual effort and response time.
Cost-Effective Threat Detection and Response
Security Center offers two pricing tiers: Free and Standard. The Free tier provides basic security posture assessment, while the Standard tier unlocks advanced threat protection, just-in-time VM access, and adaptive application controls.
With pay-as-you-go pricing for the Standard tier, organizations only pay for the resources they monitor. This makes it a cost-effective solution compared to deploying multiple standalone security tools.
Security Posture Management in Azure Security Center
Security posture management is the foundation of Azure Security Center. It helps you identify misconfigurations, enforce compliance, and maintain a strong security baseline across your infrastructure.
Security Policies and Compliance Standards
Security policies define the rules and requirements for your resources. You can customize policies per subscription or resource group, tailoring them to your organization’s needs.
Security Center includes built-in compliance controls aligned with industry standards such as CIS, NIST, ISO 27001, GDPR, and HIPAA. It also integrates with Azure Policy to enforce these rules at scale.
For example, if a virtual machine is deployed without a firewall, Security Center flags it as non-compliant and suggests remediation steps. This proactive approach prevents security gaps before they can be exploited.
Secure Score and Risk Assessment
The Secure Score is a key metric in Azure Security Center that quantifies your security posture. It’s calculated based on the percentage of recommended actions you’ve implemented.
A higher Secure Score means better protection. For instance, if Security Center recommends 100 actions and you’ve completed 85, your score would be 85%. The platform tracks this over time, helping you measure improvement.
You can also compare your score against industry benchmarks or peer organizations. This visibility encourages continuous improvement and accountability across teams.
Integration with Azure Policy and Regulatory Compliance
Azure Security Center works seamlessly with Azure Policy to enforce governance at scale. You can create custom policies or use pre-built ones from the Azure Policy initiative for security.
Additionally, the Regulatory Compliance dashboard provides detailed reports on how your environment meets specific regulatory requirements. This is invaluable for audits and compliance reporting.
Learn more about compliance in Azure at Microsoft’s Compliance Documentation.
Advanced Threat Protection with Azure Security Center
Beyond posture management, Azure Security Center excels in detecting and responding to threats in real time. It uses advanced analytics, machine learning, and behavioral monitoring to identify suspicious activities.
Real-Time Threat Detection
Azure Security Center monitors logs, network traffic, and system events to detect anomalies. It integrates with Azure Monitor and Log Analytics to collect and analyze data from your resources.
When a potential threat is detected—such as a brute force attack, malware execution, or suspicious outbound connection—Security Center generates a security alert. These alerts include details like the affected resource, attack vector, and recommended response actions.
For example, if an Azure VM starts communicating with a known malicious IP address, Security Center raises a high-severity alert and suggests blocking the connection via a network security group.
Integration with Microsoft Defender for Endpoint
Azure Security Center integrates with Microsoft Defender for Endpoint (formerly Microsoft Defender ATP) to provide endpoint detection and response (EDR) capabilities.
This integration allows Security Center to detect malicious processes, suspicious registry changes, and lateral movement attempts on Windows and Linux machines. It also enables automated investigation and remediation workflows.
By combining cloud workload protection with endpoint telemetry, organizations gain a holistic view of threats across their environment.
Automated Incident Response and Playbooks
To reduce response time, Azure Security Center supports automated incident response using Azure Logic Apps and playbooks.
For example, when a ransomware alert is triggered, a playbook can automatically isolate the affected VM, disable user accounts, and notify the security team via email or Teams. This automation minimizes damage and frees up analysts for higher-level tasks.
You can customize playbooks or use pre-built templates from the Azure Security Center marketplace.
Just-In-Time VM Access and Adaptive Application Controls
Azure Security Center introduces innovative security controls that reduce the attack surface of your virtual machines and applications.
How Just-In-Time VM Access Works
Just-In-Time (JIT) VM access is a powerful feature that locks down inbound traffic to your virtual machines. Instead of leaving ports like RDP (3389) or SSH (22) open 24/7, JIT closes them by default.
When an administrator needs access, they request it through the Azure portal. Security Center validates the request, opens the required ports for a specified time (e.g., 30 minutes), and logs the session for audit purposes.
This significantly reduces the risk of brute force attacks and unauthorized access. According to Microsoft, JIT can reduce exposure to VM attacks by up to 70%.
Benefits of JIT in Reducing Attack Surface
The primary benefit of JIT is minimizing the window of opportunity for attackers. Open ports are a common entry point for cybercriminals, especially in cloud environments where misconfigurations are frequent.
By enforcing least-privilege access and time-bound permissions, JIT aligns with zero-trust principles. It also provides detailed audit trails, helping meet compliance requirements for access control.
Adaptive Application Controls
Adaptive application controls use machine learning to identify trusted applications running on your VMs. Once a baseline is established, any unauthorized executable is blocked or alerted.
For example, if a script attempts to run PowerShell in an unusual context, Security Center flags it as suspicious. You can configure the system to allow, audit, or deny such actions.
This feature is especially useful for preventing fileless malware and living-off-the-land attacks.
Cloud Security Posture Management (CSPM) with Azure Security Center
Cloud Security Posture Management (CSPM) is a critical capability for organizations moving to the cloud. Azure Security Center is a leading CSPM solution that helps prevent misconfigurations and enforce security policies.
Continuous Monitoring and Configuration Drift Detection
Cloud environments are dynamic—resources are created, modified, and deleted constantly. This increases the risk of configuration drift, where systems deviate from secure baselines.
Azure Security Center continuously monitors your resources for changes. If a storage account is made publicly accessible or a database is deployed without encryption, Security Center detects it immediately and alerts you.
This real-time monitoring ensures that security policies are consistently enforced, even in fast-moving DevOps environments.
Multi-Cloud and Hybrid Support
While Azure Security Center originated as an Azure-native tool, it now supports hybrid and multi-cloud architectures. You can connect AWS and GCP environments using connectors and agents.
For AWS, you link your account via IAM roles, allowing Security Center to assess EC2 instances, S3 buckets, and IAM policies. For GCP, integration is done through APIs and service accounts.
This cross-cloud visibility enables centralized security management, reducing complexity for IT teams.
Role-Based Access Control and Governance
Azure Security Center supports Azure Role-Based Access Control (RBAC), allowing you to assign granular permissions to users and groups.
For example, you can grant a security analyst read-only access to alerts, while a security administrator has full control over policies and configurations. This ensures accountability and prevents unauthorized changes.
RBAC integrates with Azure Active Directory (Azure AD), enabling single sign-on and multi-factor authentication for secure access.
Integration with DevOps and CI/CD Pipelines
Modern development practices require security to be embedded early in the software lifecycle. Azure Security Center supports DevSecOps by integrating with CI/CD pipelines and infrastructure-as-code tools.
Security as Code with Azure Policy
You can define security policies as code using Azure Policy templates. These policies can be version-controlled, tested, and deployed alongside your infrastructure.
For example, a policy can enforce that all new VMs must have disk encryption enabled. If a developer tries to deploy a VM without it, the deployment fails, ensuring compliance by design.
This approach shifts security left, catching issues before they reach production.
Integration with Azure DevOps and GitHub
Azure Security Center integrates with Azure DevOps and GitHub to provide security feedback during development. You can set up pipelines to scan infrastructure templates (like ARM or Terraform) for security issues.
Security alerts can be automatically created as work items in Azure Boards, ensuring they are tracked and resolved. This closes the loop between development and security teams.
Automated Security Testing in CI/CD
By integrating Security Center APIs into your CI/CD pipeline, you can perform automated security assessments on every code commit.
For instance, after deploying a new environment to a test subscription, a script can query Security Center for any high-severity recommendations and fail the build if critical issues are found.
This ensures that only secure, compliant environments are promoted to production.
Best Practices for Maximizing Azure Security Center
To get the most out of Azure Security Center, organizations should follow proven best practices that enhance visibility, automation, and response efficiency.
Enable Standard Tier Across All Subscriptions
The Free tier provides basic visibility, but the Standard tier unlocks critical features like threat detection, JIT VM access, and adaptive application controls.
It’s recommended to enable the Standard tier across all production and critical subscriptions. You can use Azure Policy to enforce this at scale.
Regularly Review and Remediate Security Recommendations
Security recommendations are only valuable if acted upon. Set up weekly reviews to address high-severity issues first.
Use the Secure Score dashboard to track progress and set improvement goals. Assign ownership of recommendations to specific teams to ensure accountability.
Leverage Automation for Incident Response
Manual response is slow and error-prone. Use Azure Logic Apps and playbooks to automate common responses, such as isolating compromised VMs or disabling breached accounts.
Test your playbooks regularly to ensure they work as expected during real incidents.
What is Azure Security Center used for?
Azure Security Center is used to strengthen the security posture of cloud and hybrid environments. It provides security recommendations, threat detection, just-in-time VM access, and compliance management across Azure, on-premises, and multi-cloud workloads.
Is Azure Security Center free?
Azure Security Center has a Free tier that offers basic security posture assessment. However, advanced features like threat protection and JIT VM access require the Standard tier, which is billed based on resource usage.
How does Azure Security Center integrate with AWS?
Azure Security Center integrates with AWS by connecting your AWS account via IAM roles. This allows it to assess EC2 instances, S3 buckets, and IAM configurations, providing unified security visibility across clouds.
What replaced Azure Security Center?
Azure Security Center has evolved into Microsoft Defender for Cloud, which offers enhanced capabilities including multi-cloud support, expanded threat protection, and deeper integration with Microsoft 365 Defender. However, the core functionality remains the same.
How do I improve my Secure Score in Azure Security Center?
To improve your Secure Score, implement high-severity recommendations first, enable the Standard tier, enforce security policies via Azure Policy, and regularly review and remediate vulnerabilities. Automation and continuous monitoring also help maintain a high score.
Azure Security Center—now part of Microsoft Defender for Cloud—is a powerful, comprehensive solution for securing modern cloud environments. From posture management to advanced threat detection, it empowers organizations to stay ahead of cyber threats. By leveraging its full capabilities, including JIT access, adaptive controls, and automation, businesses can build a resilient, proactive security strategy. Whether you’re running Azure-only workloads or managing a complex hybrid infrastructure, Azure Security Center provides the visibility, control, and intelligence needed to protect your digital assets.
Further Reading: