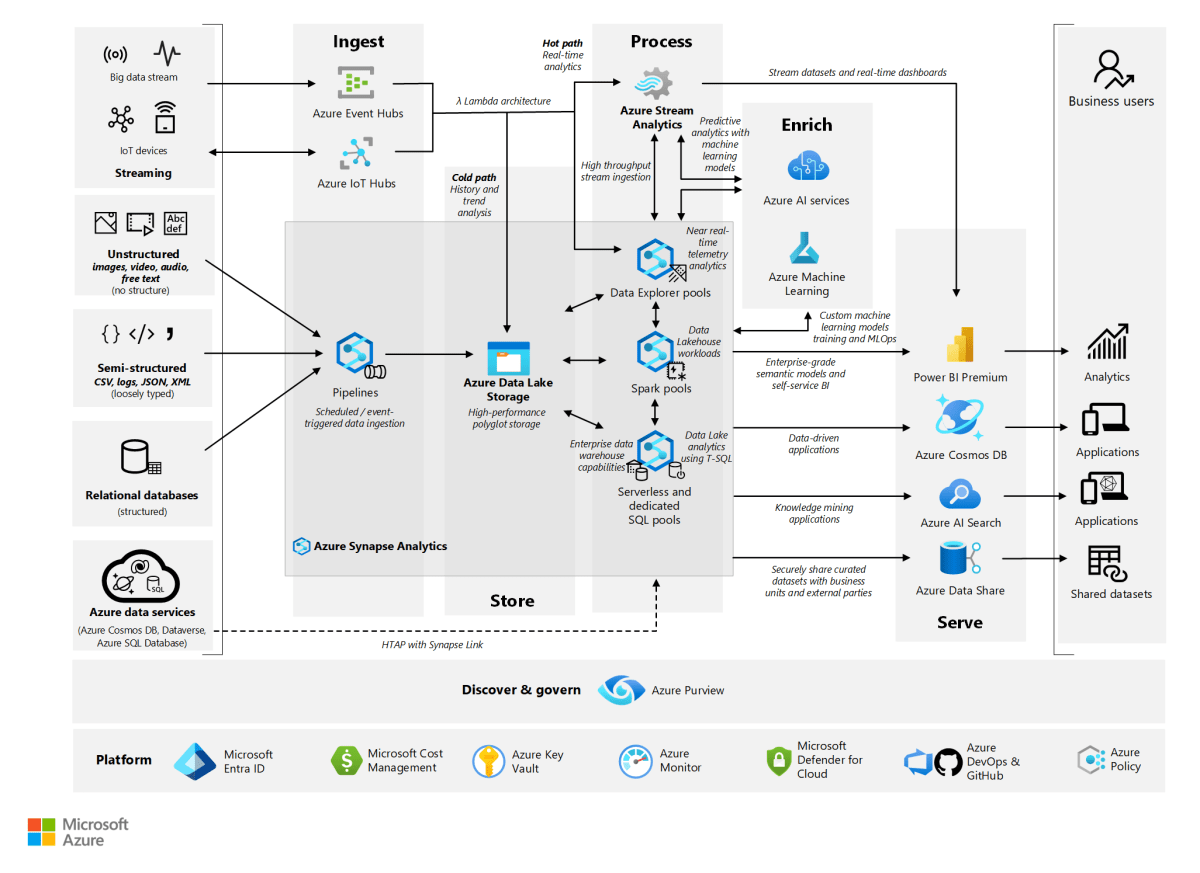
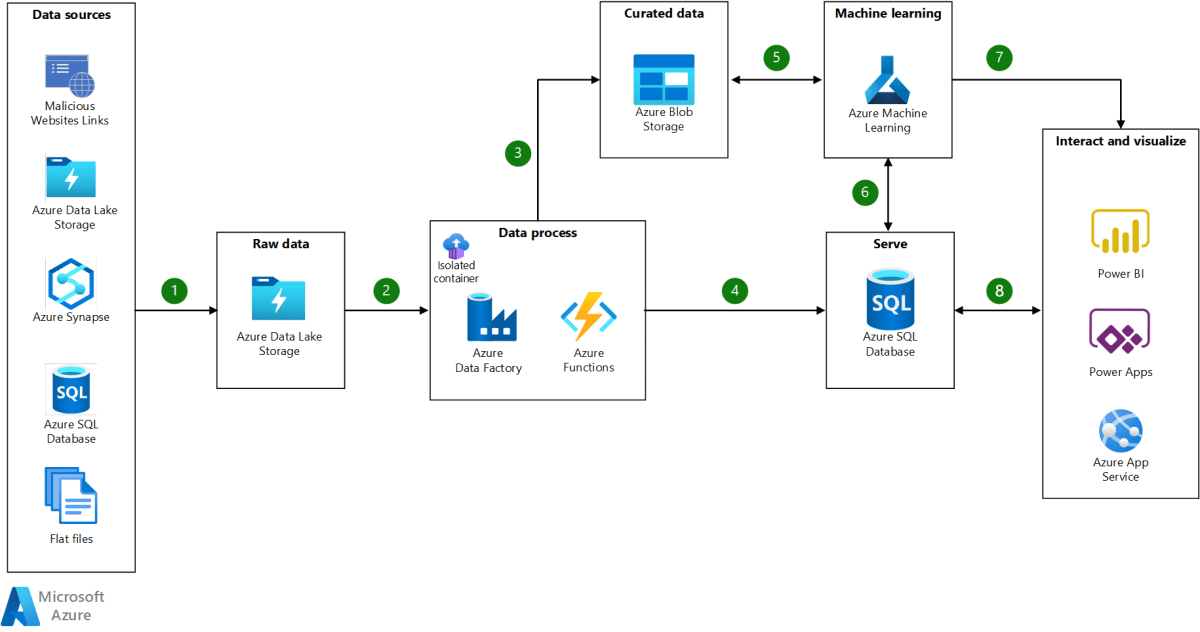
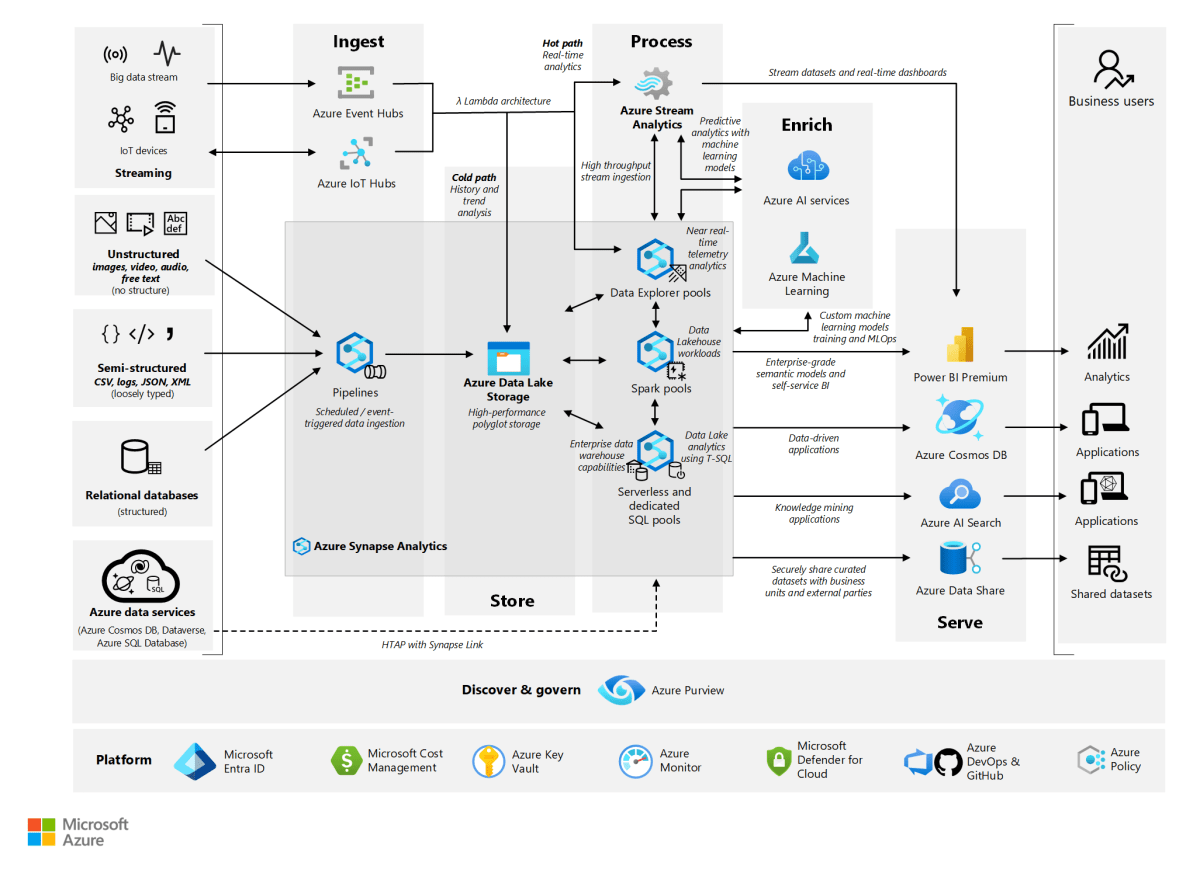
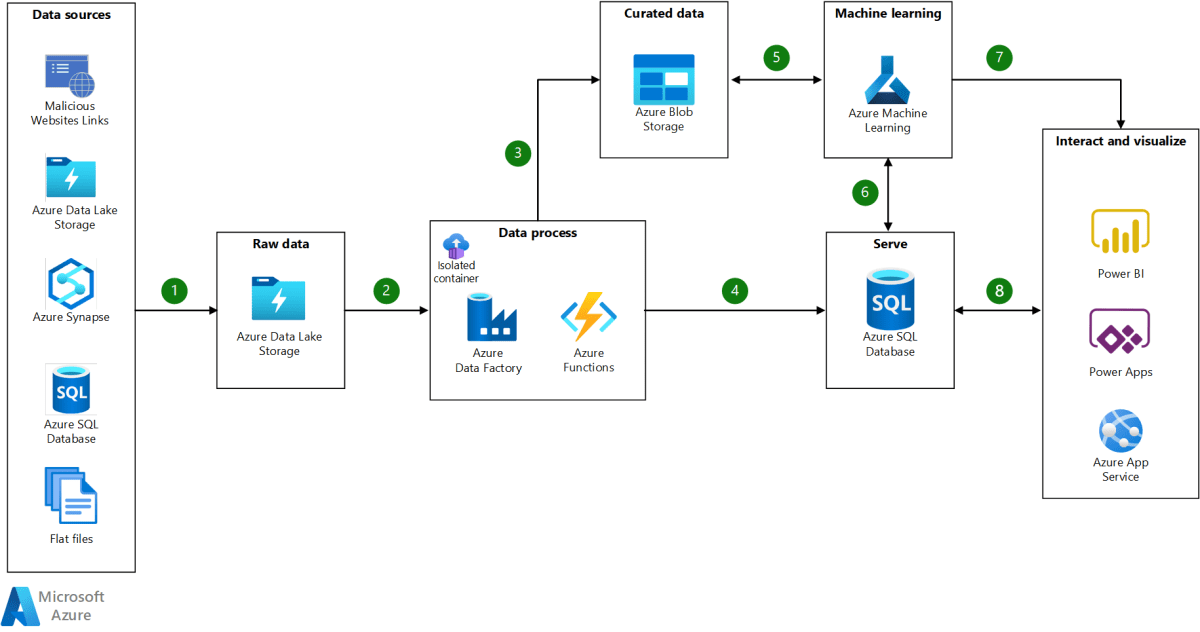
Azure Virtual Network : 7 Powerful Insights You Must Know
Welcome to the world of cloud networking—where Azure Virtual Network (VNet) acts as the backbone of your cloud infrastructure. Think of it as your private neighborhood in the vast city of the cloud, where your apps, VMs, and services live securely, connected and isolated from the chaos outside. Let’s dive in.
What Is Azure Virtual Network (VNet)?
An Azure Virtual Network (VNet) is the fundamental building block for private networks in Microsoft Azure. It enables Azure resources like virtual machines (VMs), app services, and containers to securely communicate with each other, the internet, and on-premises networks. Essentially, a VNet is your slice of the Azure cloud, logically isolated from other customers.
Core Definition and Purpose
Azure Virtual Network (VNet) provides a secure, isolated environment where you can deploy and manage Azure resources in a private network space. It allows you to define IP address ranges, subnets, and routing rules, giving you full control over network behavior in the cloud.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
- Acts as a private network in the Azure cloud
- Enables communication between Azure resources
- Supports hybrid connectivity to on-premises networks
“Azure Virtual Network is the foundation of network security and segmentation in Azure.” — Microsoft Azure Documentation
How VNet Works in the Cloud Ecosystem
When you create a VNet, you define a private IP address space using CIDR notation (e.g., 10.0.0.0/16). Within this space, you can create subnets to organize and segment resources. Each subnet can host different types of Azure resources, such as VMs, Azure Kubernetes Service (AKS), or Azure App Service Environments.
Resources within the same VNet can communicate seamlessly, while traffic between VNets or to external networks is controlled through routing, network security groups (NSGs), and firewalls.
For example, a web server in one subnet can securely talk to a database in another subnet, all within the same VNet, without exposing data to the public internet.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Azure Virtual Network (VNet) Key Features and Capabilities
The power of Azure Virtual Network (VNet) lies in its rich set of features that enable secure, scalable, and flexible networking in the cloud. From IP management to advanced routing, VNet gives you enterprise-grade control.
IP Address Management and Subnetting
One of the first steps in setting up a VNet is defining your IP address space. You can use private IP ranges from RFC 1918:
- 10.0.0.0 – 10.255.255.255 (10/8 prefix)
- 172.16.0.0 – 172.31.255.255 (172.16/12 prefix)
- 192.168.0.0 – 192.168.255.255 (192.168/16 prefix)
Within the VNet, you can divide the address space into subnets. Each subnet serves as a segment for specific workloads—like web, app, or database tiers.
For instance, you might allocate 10.0.1.0/24 for web servers and 10.0.2.0/24 for databases, ensuring logical separation and easier security management.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Network Security Groups (NSGs) and Application Security
Network Security Groups (NSGs) are essential for controlling inbound and outbound traffic to subnets or individual network interfaces. You can define rules based on source/destination IP, port, and protocol.
For example, you can allow HTTP (port 80) and HTTPS (port 443) traffic to a web subnet while blocking all inbound traffic to a database subnet except from the app tier.
NSGs work at the subnet or NIC level and are stateful—meaning if you allow outbound traffic, the corresponding inbound response is automatically permitted.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
User-Defined Routing (UDR)
By default, Azure handles routing within and between VNets automatically. However, for advanced scenarios, you can use User-Defined Routes (UDRs) to override default routes.
For example, you might route all traffic through a virtual appliance (like a firewall or IDS/IPS) for inspection before it reaches its destination. This is crucial for organizations needing deep packet inspection or compliance with strict security policies.
UDRs are associated with subnets and allow you to define next-hop types such as virtual appliances, virtual network gateways, or internet endpoints.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Azure Virtual Network (VNet) Peering: Connecting Networks Seamlessly
VNet peering allows two VNets to be connected, enabling resources in both to communicate as if they were on the same network. This is one of the most powerful features for building scalable, multi-tier, or multi-region architectures.
What Is VNet Peering?
VNet peering creates a high-speed, low-latency connection between two VNets in the same region (regional peering) or across different regions (global peering). Once peered, the VNets share the same routing information, and traffic flows through Microsoft’s backbone network—never over the public internet.
This is ideal for scenarios like separating development and production environments while allowing controlled communication, or connecting VNets in different subscriptions.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Benefits of VNet Peering
- High Performance: Traffic between peered VNets uses the Microsoft backbone, ensuring low latency and high bandwidth.
- No Public Internet Exposure: Communication stays within Azure’s private network.
- Cross-Subscription Support: You can peer VNets across different Azure subscriptions, even under different Azure AD tenants.
- Transitive Peering Support via Hub-Spoke: With Azure Virtual WAN or hub-spoke topologies, you can enable transitive connectivity.
For example, a hub VNet can host shared services like firewalls or DNS servers, while multiple spoke VNets (for apps, data, etc.) peer with the hub for centralized control.
Limitations and Best Practices
While VNet peering is powerful, it has some limitations:
- Peering is not transitive by default. If VNet A is peered with B, and B with C, A cannot talk to C unless you enable transitive routing via a network virtual appliance (NVA).
- Address spaces must not overlap between peered VNets.
- There’s a limit to the number of peerings per VNet (currently 500).
Best practices include using non-overlapping IP ranges, monitoring peering health, and leveraging NSGs for granular traffic control.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Hybrid Connectivity: Bridging On-Premises and Azure
For most enterprises, the cloud isn’t a replacement—it’s an extension. Azure Virtual Network (VNet) supports seamless hybrid connectivity, allowing you to integrate on-premises data centers with your cloud environment.
Site-to-Site (S2S) VPN
A Site-to-Site VPN connects your on-premises network to an Azure VNet over an IPsec/IKE encrypted tunnel. This is ideal for organizations that want secure, always-on connectivity without high costs.
You need a compatible VPN device on-premises and a Virtual Network Gateway in Azure. Once configured, your on-premises users and systems can access Azure resources as if they were local.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
For example, a company with a data center in New York can securely connect to its Azure VNet in East US, enabling hybrid applications and data replication.
ExpressRoute for Private, High-Performance Links
ExpressRoute offers a private connection between your on-premises infrastructure and Azure, bypassing the public internet. It provides higher reliability, faster speeds, and lower latencies than typical internet connections.
ExpressRoute supports bandwidths from 50 Mbps to 10 Gbps and connects through service providers like AT&T, Equinix, or BT.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Use cases include migrating large datasets, running latency-sensitive applications, or meeting compliance requirements that prohibit data from traversing the public internet.
Learn more about ExpressRoute capabilities at Microsoft’s ExpressRoute documentation.
Point-to-Site (P2S) VPN for Remote Users
Point-to-Site VPN allows individual devices to connect securely to an Azure VNet over the internet. This is perfect for remote workers or developers who need access to cloud resources without setting up a full site-to-site connection.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
P2S uses SSTP or IKEv2 protocols and integrates with Azure AD for authentication, enhancing security and ease of use.
For example, a developer working from home can connect to the dev VNet to debug a VM or deploy code, all without exposing the VM to the public internet.
Advanced Networking with Azure Virtual Network (VNet)
As your cloud environment grows, so do your networking needs. Azure Virtual Network (VNet) supports advanced scenarios like network virtual appliances, service endpoints, private endpoints, and integration with Azure Firewall.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Service Endpoints and Private Endpoints
Service Endpoints allow you to secure your Azure PaaS services (like Azure Storage or SQL Database) by restricting access to specific VNets. Instead of exposing these services to the public internet, you can lock them down to only accept traffic from your VNet.
Private Endpoints take this further by assigning a private IP address from your VNet to the service, making it appear as if the service is hosted inside your network. This is known as Azure Private Link.
For example, you can create a private endpoint for an Azure SQL server so that only VMs in your VNet can access it, with no public IP required.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Network Virtual Appliances (NVAs)
Network Virtual Appliances are third-party or Microsoft-provided VMs that perform advanced networking functions like firewalling, intrusion detection, WAN optimization, or SD-WAN.
You can deploy NVAs in your VNet and use User-Defined Routes to direct traffic through them. For example, a Palo Alto firewall NVA can inspect all traffic between subnets for threats.
Popular NVAs include Barracuda, Check Point, Fortinet, and Cisco CSR. These integrate seamlessly with Azure’s routing and NSG features.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Integration with Azure Firewall and DDoS Protection
Azure Firewall is a managed, cloud-native firewall service that provides high-availability and built-in threat intelligence. It can filter traffic at the application and network layer, support SNAT/DNAT, and integrate with Azure Monitor for logging.
When combined with VNet, Azure Firewall can protect all outbound and inbound traffic, especially in hub-spoke architectures.
Additionally, Azure DDoS Protection helps safeguard your applications from distributed denial-of-service attacks. When enabled, it automatically detects and mitigates attacks in real time.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Learn more about Azure Firewall at Azure Firewall Overview.
Security and Compliance in Azure Virtual Network (VNet)
Security is not an afterthought—it’s built into the design of Azure Virtual Network (VNet). From encryption to role-based access control, Azure provides multiple layers of protection.
Network Security Groups vs. Azure Firewall
While both NSGs and Azure Firewall control traffic, they serve different purposes:
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
- NSGs: Best for basic allow/deny rules at the subnet or NIC level. They operate at layers 3 and 4 (IP, port).
- Azure Firewall: A full-stateful firewall with application-level filtering (layer 7), URL filtering, and threat intelligence. Ideal for centralized security policies.
In practice, many organizations use NSGs for micro-segmentation and Azure Firewall for perimeter defense.
Role-Based Access Control (RBAC) and Network Policies
Azure’s Role-Based Access Control (RBAC) allows you to assign granular permissions to users and services. For example, you can grant a network administrator full access to VNets while restricting developers to read-only access.
You can also use Azure Policy to enforce network compliance rules, such as “All VNets must have DDoS protection enabled” or “No public IP on database subnets.”
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
This ensures consistent governance across large, multi-team environments.
Data Encryption and Traffic Protection
All traffic within a VNet is private and isolated. However, for sensitive data, you should still use encryption:
- In-transit: Use TLS/SSL for application traffic, IPsec for site-to-site VPNs.
- At-rest: Enable encryption on VM disks (Azure Disk Encryption) and databases.
Azure also supports MACsec (Media Access Control Security) for ExpressRoute connections, providing link-layer encryption between your on-premises and Azure.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Monitoring, Troubleshooting, and Best Practices
Even the best-designed networks need monitoring. Azure provides tools to help you track performance, diagnose issues, and optimize your VNet setup.
Azure Network Watcher
Azure Network Watcher is a monitoring service that helps you diagnose and troubleshoot network issues. Key features include:
- Connection Troubleshoot: Test connectivity between a VM and another endpoint (IP, port, URL).
- IP Flow Verify: Check if a traffic rule in an NSG is blocking or allowing traffic.
- Packet Capture: Capture network packets from a VM for deep analysis.
- Topology Visualization: See a graphical view of your VNet, subnets, NSGs, and connected resources.
For example, if a VM can’t reach a database, you can use Connection Troubleshoot to identify whether it’s a routing, firewall, or NSG issue.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Logging and Analytics with Azure Monitor
Azure Monitor collects logs from NSGs, firewalls, and VNets, allowing you to analyze traffic patterns, detect anomalies, and set up alerts.
You can use Log Analytics to run queries like:
“Show all denied inbound traffic on port 22 over the last 24 hours”
This helps in identifying potential security threats or misconfigurations.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Best Practices for Azure Virtual Network (VNet)
Plan Your IP Addressing: Use a consistent IP schema across VNets to avoid conflicts, especially in hybrid or multi-region setups.Adopt a Hub-Spoke Model: Centralize shared services and security in a hub VNet, with spoke VNets for workloads.Use Private Endpoints for PaaS Services: Minimize exposure of Azure services to the public internet.Enable DDoS Protection: Especially for public-facing applications..
Regularly Audit NSG Rules: Remove unused or overly permissive rules.Monitor Peering Health: Use Azure Monitor to detect peering disconnections or latency spikes.Real-World Use Cases of Azure Virtual Network (VNet)
Theoretical knowledge is great, but real-world applications show the true power of Azure Virtual Network (VNet).Let’s explore how organizations use it in practice..
Enterprise Hybrid Cloud Architecture
A global bank uses ExpressRoute to connect its data centers in London, Tokyo, and New York to Azure VNets in corresponding regions. Each VNet hosts critical applications like core banking, customer portals, and fraud detection systems.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
The hub-spoke model is used, with a central hub VNet hosting firewalls, DNS, and monitoring tools. Spoke VNets for different departments (retail, corporate, compliance) peer with the hub, ensuring secure, segmented access.
Disaster Recovery and Multi-Region Deployment
An e-commerce company runs its primary application in East US with a VNet hosting web, app, and database tiers. A secondary VNet in West US acts as a disaster recovery site.
VNet peering (global) and Azure Site Recovery ensure that if the primary region fails, traffic is rerouted to the secondary site with minimal downtime.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Secure Development and Testing Environments
A software firm uses separate VNets for development, testing, and production. Each VNet has identical subnets but isolated security policies.
Developers connect via Point-to-Site VPN to the dev VNet, while automated CI/CD pipelines deploy to test and production VNets using service principals and RBAC.
What is Azure Virtual Network (VNet)?
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Azure Virtual Network (VNet) is a service that provides a private, isolated network environment in Microsoft Azure. It allows you to launch Azure resources in a virtual network, define IP ranges, subnets, and control traffic flow using security groups and routing rules.
How does VNet peering work?
VNet peering connects two Azure virtual networks, enabling resources to communicate using private IP addresses. Traffic flows over the Microsoft backbone network, not the public internet. Peering can be regional or global and supports cross-subscription connectivity.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Can I connect my on-premises network to Azure VNet?
Yes, you can connect your on-premises network to Azure VNet using Site-to-Site VPN, Point-to-Site VPN, or ExpressRoute. ExpressRoute provides a private, high-speed connection without going over the internet.
What is the difference between NSG and Azure Firewall?
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Network Security Groups (NSGs) provide basic layer 3 and 4 filtering for subnets and NICs. Azure Firewall is a managed, cloud-native firewall service with advanced features like application-level filtering, threat intelligence, and centralized policy management.
How do I secure Azure PaaS services like Storage or SQL?
You can secure PaaS services using Service Endpoints (to restrict access to specific VNets) or Private Endpoints (to assign a private IP from your VNet to the service, making it accessible only within your network).
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Azure Virtual Network (VNet) is far more than just a cloud network—it’s the foundation of secure, scalable, and intelligent connectivity in Azure. From simple VM deployments to complex hybrid and multi-region architectures, VNet provides the flexibility and control enterprises demand. By leveraging features like peering, hybrid connectivity, private endpoints, and advanced security, you can build a resilient and future-proof cloud infrastructure. Whether you’re a network engineer, cloud architect, or developer, mastering Azure Virtual Network (VNet) is essential for success in the Azure ecosystem.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Recommended for you 👇
Further Reading: